Utilize information and threat detection strategies to obtain the upper hand.
Introducing the CompTIA Cybersecurity Analyst (CySA+) certification – your passport to an exhilarating career in the ever-evolving world of cybersecurity! With the relentless rise in cyber threats from malicious actors, organizations are seeking skilled professionals to safeguard their digital assets. CySA+ empowers you with the knowledge and skills needed to excel in this high-demand field.
Join the League of cybersecurity superheroes and gain an in-depth understanding of the fundamentals that form the bedrock of effective cybersecurity. CySA+ equips you with the expertise to perform a range of crucial tasks, ensuring your organization stays one step ahead of cybercriminals.
Become a master of threat and vulnerability management, discovering how to identify and analyze potential risks lurking within networks, systems, and applications. With this knowledge, you’ll be able to proactively shield organizations from potential attacks, saving them from disastrous consequences.
Immerse yourself in the world of security operations and monitoring, and witness firsthand the power of constant vigilance. CySA+ unveils the secrets of effective security event monitoring, incident detection, and swift response strategies. You’ll learn to navigate through complex security incidents like a seasoned professional, minimizing damage and restoring normalcy in record time.
Delve into the realm of security architecture and tool sets, where you’ll learn to design robust security frameworks that fortify organizations against even the most advanced threats. CySA+ equips you with the expertise to select and deploy cutting-edge security technologies, ensuring that your organization has a formidable defense against cyber adversaries.
But the journey doesn’t stop there! To truly showcase your cybersecurity prowess, you’ll need to conquer the CySA+ exam. This comprehensive assessment evaluates your knowledge and practical skills across the certification’s domains. Demonstrate your abilities, and upon successful completion, earn the prestigious CySA+ certification, instantly boosting your professional credibility and opening doors to exciting career opportunities.
Join the ranks of elite cybersecurity professionals and be at the forefront of protecting the digital world. Embrace the CySA+ certification and embark on a thrilling journey filled with continuous learning, rapid growth, and the satisfaction of knowing that your skills are making a tangible difference in the battle against cyber threats.
Remember, in the world of cybersecurity, the future belongs to the brave, the skilled, and the certified. Take the leap with CySA+ today and unlock a world of endless possibilities!
CySA+ focuses on the fundamentals of cyber security and equips you with the knowledge and abilities necessary to carry out the following tasks:
- Configure and use threat-detection tools to develop threat intelligence analysts
- Perform data analysis and deploy threat detection techniques
- Interpreting the results and presenting vulnerability analysts along with vulnerability management activities to mitigate cyber threats.
The main objective of a cybersecurity analyst is to protect the network environments, applications, and systems of a company. You will stand out from your peers in your IT profession if you have the practical skills to recognize and implement IT settings that effectively defend against agents’ network assault techniques.
Regarding CompTIA CySA+
An impartial certification is CompTIA CySA+. A student often possesses Security+ or comparable expertise, as well as three to four years of experience in a related IT industry. In this regard, the CompTIA CySA+ exam sits in between the CompTIA Security+ and CompTIA Advanced Security Practitioner (CASP) examinations. When the CompTIA Security+ is insufficient but before beginning the CASP, it makes a great bridge exam.
For government organizations, cybersecurity certification is a continuing need. The CompTIA CySA+ was created with the goal of fulfilling government certification criteria for IT personnel or contractors. You can demonstrate a deeper awareness of security best practices and protocols than is implied by the Security+ certification by earning a cybersecurity certification. You will demonstrate knowledge above the average.
This makes it possible for any IT worker to demonstrate that they have a deeper awareness of enterprise security procedures and the tools required for organizational risk mitigation. The IT course’s modules are in line with the certification’s stated goals. The course goes beyond what is included in the certification. It also offers instances from real life and points that point the way for more research. Students will be better able to comprehend the certification material as well as get a fundamental understanding that they may use for practical applications.
Course Outline:
Module 1: Threat Management
Introduction
Given a scenario, apply environmental reconnaissance techniques using appropriate tools and processes Part 1
Given a scenario, apply environmental reconnaissance techniques using appropriate tools and processes Part 2
Given a scenario, apply environmental reconnaissance techniques using appropriate tools and processes Part 3
Given a scenario, apply environmental reconnaissance techniques using appropriate tools and processes Part 4
Given a scenario, apply environmental reconnaissance techniques using appropriate tools and processes Part 5
Given a scenario, apply environmental reconnaissance techniques using appropriate tools and processes Part 6
Given a scenario, apply environmental reconnaissance techniques using appropriate tools and processes Part 7
Given a scenario, apply environmental reconnaissance techniques using appropriate tools and processes Part 8
Given a scenario, apply environmental reconnaissance techniques using appropriate tools and processes Part 9
Given a scenario, analyze the results of a network reconnaissance Part 1
Given a scenario, analyze the results of a network reconnaissance Part 2
Given a scenario, analyze the results of a network reconnaissance Part 3
Given a scenario, analyze the results of a network reconnaissance Part 4
Given a scenario, analyze the results of a network reconnaissance Part 5
Given a network-based threat, implement or recommend the appropriate response and countermeasure Part 1
Given a network-based threat, implement or recommend the appropriate response and countermeasure Part 2
Given a network-based threat, implement or recommend the appropriate response and countermeasure Part 3
Given a network-based threat, implement or recommend the appropriate response and countermeasure Part 4
Explain the purpose of practices used to secure a corporate environment Part 1
Explain the purpose of practices used to secure a corporate environment Part 2
Explain the purpose of practices used to secure a corporate environment Part 3
Explain the purpose of practices used to secure a corporate environment Part 4
Module 2: Vulnerability Management
Given a scenario, implement an information security vulnerability management process Part 1
Given a scenario, implement an information security vulnerability management process Part 2
Given a scenario, implement an information security vulnerability management process Part 3
Given a scenario, implement an information security vulnerability management process Part 4
Given a scenario, implement an information security vulnerability management process Part 5
Given a scenario, implement an information security vulnerability management process Part 6
Given a scenario, implement an information security vulnerability management process Part 7
Given a scenario, analyze the output resulting from a vulnerability scan Part 1
Given a scenario, analyze the output resulting from a vulnerability scan Part 2
Compare and contrast common vulnerabilities found in the following targets within an organization Part 1
Compare and contrast common vulnerabilities found in the following targets within an organization Part 2
Compare and contrast common vulnerabilities found in the following targets within an organization Part 3
Module 3: Cyber Incident Response
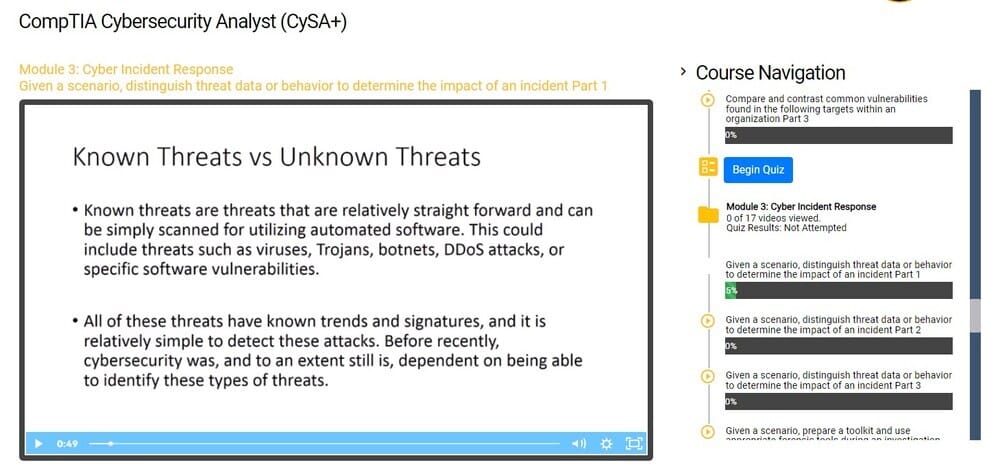
Given a scenario, distinguish threat data or behavior to determine the impact of an incident Part 1
Given a scenario, distinguish threat data or behavior to determine the impact of an incident Part 2
Given a scenario, distinguish threat data or behavior to determine the impact of an incident Part 3
Given a scenario, prepare a toolkit and use appropriate forensic tools during an investigation Part 1
Given a scenario, prepare a toolkit and use appropriate forensic tools during an investigation Part 2
Given a scenario, prepare a toolkit and use appropriate forensic tools during an investigation Part 3
Given a scenario, prepare a toolkit and use appropriate forensic tools during an investigation Part 4
Given a scenario, prepare a toolkit and use appropriate forensic tools during an investigation Part 5
Explain the importance of communication during the incident response process
Given a scenario, analyze common symptoms to select the best course of action to support incident response Part 1
Given a scenario, analyze common symptoms to select the best course of action to support incident response Part 2
Given a scenario, analyze common symptoms to select the best course of action to support incident response Part 3
Given a scenario, analyze common symptoms to select the best course of action to support incident response Part 4
Summarize the incident recovery and post-incident response process Part 1
Summarize the incident recovery and post-incident response process Part 2
Summarize the incident recovery and post-incident response process Part 3
Summarize the incident recovery and post-incident response process Part 4
Module 4: Security Architecture and Tool Sets
Explain the relationship between frameworks, common policies, controls, and procedures Part 1
Explain the relationship between frameworks, common policies, controls, and procedures Part 2
Explain the relationship between frameworks, common policies, controls, and procedures Part 3
Explain the relationship between frameworks, common policies, controls, and procedures Part 4
Given a scenario, use data to recommend remediation of security issues related to identity and access management Part 1
Given a scenario, use data to recommend remediation of security issues related to identity and access management Part 2
Given a scenario, use data to recommend remediation of security issues related to identity and access management Part 3
Given a scenario, use data to recommend remediation of security issues related to identity and access management Part 4
Given a scenario, review security architecture and make recommendations to implement compensating controls Part 1
Given a scenario, review security architecture and make recommendations to implement compensating controls Part 2
Given a scenario, review security architecture and make recommendations to implement compensating controls Part 3
Given a scenario, use applications security best practices while participating in the Software Development Life Cycle (SDLC) Part 1
Given a scenario, use applications security best practices while participating in the Software Development Life Cycle (SDLC) Part 2
Overview
Conclusion