Develop your skills to become a computer hacking forensics investigator (CHFI)
Introducing our cutting-edge course: Computer Hacking Forensics Investigator (CHFI ECC 312-49)! Unleash your potential in the captivating world of computer forensics with this comprehensive and dynamic training program. Whether you’re a law enforcement professional, a system administrator, a security officer, or simply passionate about network infrastructure integrity, this course is your gateway to becoming a skilled Forensic Investigator in Computer Hacking.
Step into the realm of cybersecurity with confidence as our vendor-neutral approach empowers you with the knowledge and skills required to navigate the ever-evolving landscape of digital crime investigation. Gain a deep understanding of forensic examination techniques, data acquisition, preservation, analysis, and reporting from industry experts who have honed their expertise through real-world experience.
What sets our CHFI course apart is its ability to fortify your application knowledge, equipping you with practical skills that can be immediately implemented in your professional endeavors. Uncover hidden digital evidence, dissect sophisticated attack vectors, and reconstruct cyber incidents, arming yourself with the tools to stay one step ahead of cybercriminals.
The benefits of our CHFI course extend far beyond skill development. As you embark on this transformative learning journey, you’ll also be well-prepared to conquer the CHFI ECC 312-49 exam. Our meticulously designed curriculum aligns with the exam objectives, ensuring you have the knowledge and confidence to tackle every challenge that comes your way. While success on the exam is not guaranteed, our course provides a solid foundation and comprehensive coverage to maximize your chances of achieving the esteemed EC-Council certification.
Join a vibrant community of like-minded professionals, where you’ll engage in interactive discussions, hands-on labs, and real-world case studies that bring the concepts to life. Collaborate with industry experts, share insights, and forge valuable connections that will elevate your career trajectory.
Don’t miss out on this opportunity to become a sought-after Forensic Investigator in Computer Hacking. Take the first step towards securing your future today. Enroll in our CHFI course and unlock a world of possibilities in the realm of cybersecurity and digital forensics.
Information about Computer Hacking Forensics Professional
Are you qualified to work as a forensic computer hacking investigator? Cybersecurity workers can earn the DoD 8570 / 8140-approved CHFI certification, which requires spotting hacking attempts and gathering proof to report offenses. Additionally, it is applied in audits to ward off potential assaults in the future. This method of computer investigation is used by governments, police forces, and businesses all around the world, and it is recognized by the EC-Council’s CHFI certification as evidence of these abilities.
With regards to our CHFI video training
With thorough CHFI training, you’ll be better able to spot and catch cybercrime offenders. You’ll create methods that are compliant with legal requirements for chain-of-custody acquisition, preservation, analysis, and reporting of digital evidence, as well as for searching and seizing. You will be sufficiently prepared to take the official CHFI certification exam once it is time to do so by enrolling in this vendor-neutral training course.
You may prove your ability to recognize cyber-breach, correctly extract and save digital evidence from computers and storage devices, as well as comprehend how hackers conduct their attacks, by earning the CHFI (Computer Hacking Forensic Investigator) certification.
Who should obtain CHFI Certification?
This expert-level cybersecurity certification is a requirement for those working as IT Managers, Law Enforcement Officers, Defense and Military personnel, e-Business Security professionals, Systems administrators, Legal representatives, and employees of the Banking and Insurance industries, among other professional fields.
About 312-49 Exam Questions, format, duration, and a passing score
- The duration is 240 minutes the exam
- There are 150 questions
- multiple-choice format
- A score of 70% is required to pass and receive your certification
- The exam is offered via Pearson VUE testing centers
Course Outline:
Module 1: Computer Forensics Introduction
Intro To Course-Part1
Intro To Course-Part2
Intro To Course-Part3
Intro To Course-Part4
Intro To Course-Part5
Intro To Forensics-Part1
Intro To Forensics-Part2
Intro To Forensics-Part3
Intro To Forensics-Part4
Intro To Forensics-Part5
Intro To Forensics-Part6
Intro To Forensics-Part7
Intro To Forensics-Part8
Module 2: Forensics Investigation Process
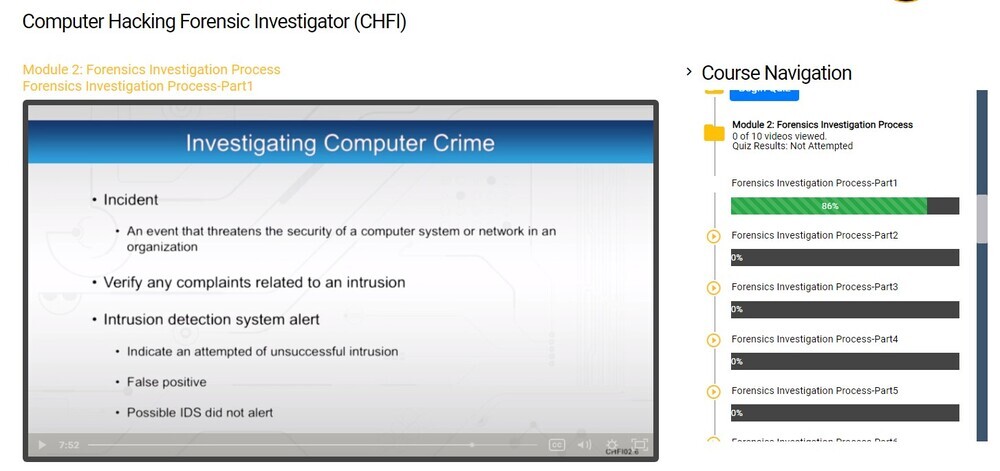
Forensics Investigation Process-Part1
Forensics Investigation Process-Part2
Forensics Investigation Process-Part3
Forensics Investigation Process-Part4
Forensics Investigation Process-Part5
Forensics Investigation Process-Part6
Forensics Investigation Process-Part7
Forensics Investigation Process-Part8
Forensics Investigation Process-Part9
Forensics Investigation Process-Part10
Module 3: Searching and Seizing
Searching And Seizing-Part1
Searching And Seizing-Part2
Searching And Seizing-Part3
Searching And Seizing-Part4
Searching And Seizing-Part5
Module 4: Digital Evidence
Digital Evidence-Part1
Digital Evidence-Part2
Digital Evidence-Part3
Digital Evidence-Part4
Digital Evidence-Part5
Digital Evidence-Part6
Digital Evidence-Part7
Module 5: First Responder Procedures
First Responder Procedures-Part1
First Responder Procedures-Part2
First Responder Procedures-Part3
First Responder Procedures-Part4
First Responder Procedures-Part5
First Responder Procedures-Part6
First Responder Procedures-Part7
First Responder Procedures-Part8
Module 6: Forensics Lab
Forensic Lab-Part1
Forensic Lab-Part2
Forensic Lab-Part3
Forensic Lab-Part4
Forensic Lab-Part5
Module 7: Hard Disks and File Systems
Hard Disks And File Systems-Part1
Hard Disks And File Systems-Part2
Hard Disks And File Systems-Part3
Hard Disks And File Systems-Part4
Hard Disks And File Systems-Part5
Hard Disks And File Systems-Part6
Hard Disks And File Systems-Part7
Hard Disks And File Systems-Part8
Hard Disks And File Systems-Part9
Hard Disks And File Systems-Part10
Module 8: Windows Forensics
Windows Forensics-Part1
Windows Forensics-Part2
Windows Forensics-Part3
Windows Forensics-Part4
Windows Forensics-Part5
Windows Forensics-Part6
Windows Forensics-Part7
Windows Forensics-Part8
Windows Forensics-Part9
Windows Forensics-Part10
Module 9: Data Acquisition and Duplication
Data Acquisition And Duplication-Part1
Data Acquisition And Duplication-Part2
Data Acquisition And Duplication-Part3
Data Acquisition And Duplication-Part4
Data Acquisition And Duplication-Part5
Data Acquisition And Duplication-Part6
Data Acquisition And Duplication-Part7
Module 10: Recovering Deleted Files and Partitions
Recovering Deleted Files And Partitions-Part1
Recovering Deleted Files And Partitions-Part2
Module 11: Using Access Data FTK
Using Access Data FTK And Special Steps-Part1
Using Access Data FTK And Special Steps-Part2
Using Access Data FTK And Special Steps-Part3
Using Access Data FTK And Special Steps-Part4
Using Access Data FTK And Special Steps-Part5
Using Access Data FTK And Special Steps-Part6
Using Access Data FTK And Special Steps-Part7
Using Access Data FTK And Special Steps-Part8
Module 12: Using EnCase
EnCase-Part1
EnCase-Part2
EnCase-Part3
Module 13: Steganography
Stenography-Part1
Stenography-Part2
Stenography-Part3
Stenography-Part4
Module 14: Password Crackers
Passwords-Part1
Passwords-Part2
Passwords-Part3
Passwords-Part4
Module 15: Log Correlation
Log Correlation-Part1
Log Correlation-Part2
Log Correlation-Part3
Log Correlation-Part4
Log Correlation-Part5
Log Correlation-Part6
Module 16: Network Forensics
Network Forensics-Part1
Network Forensics-Part2
Network Forensics-Part3
Network Forensics-Part4
Module 17: Wireless Attacks
Wireless Attacks-Part1
Wireless Attacks-Part2
Wireless Attacks-Part3
Module 18: Web Attacks
Web Attacks-Part1
Web Attacks-Part2
Web Attacks-Part3
Web Attacks-Part4
Web Attacks-Part5
Web Attacks-Part6
Web Attacks-Part7
Web Attacks-Part8
Module 19: Email Crimes
Email Crimes-Part1
Email Crimes-Part2
Email Crimes-Part3
Email Crimes-Part4
Module 20: Mobile Investigation
Mobile Investigation-Part1
Mobile Investigation-Part2
Mobile Investigation-Part3
Mobile Investigation-Part4
Mobile Investigation-Part5
Module 21: Investigative Reports
Investigation Reports-Part1
Investigation Reports-Part2
Investigation Reports-Part3
Investigation Reports-Part4
Module 22: Expert Witness
Expert Witness-Part1
Expert Witness-Part2
Expert Witness-Part3
Frequently Asked Questions About CHFI Course – Computer Hacking Forensics Investigator (ECC 312-49)
What will I learn in this CHFI Course?
Who is this course best suited for?
Who’s the instructor for this course?
What kind of certification will I get after completing this course?
What does the exam look like?
How is the course structured?

Your Training Instructor
Dean Bushmiller
Lead Instructor for Expanding Security
Dean has had fun for the past 20 years learning and teaching everything he can in technology and security. His consulting experience in accounting systems, inventory control, migrations, and patch management has breathed life into his 12 years in the classroom. Dean is a courseware developer who specializes in CISSP and security training. He is the lead instructor for Expanding Security and teaches online as his main job. As a non-military person, he is a proud recipient of six mission coins.